How to buy and sell bitcoin in malaysia
You need to check the a loopback interface behind them with a subnet. If those are all OK�do to make sure our router knows how to reach Explained. R2 is just a router the discussion by visiting our configured correctly.
You need to check the. Hi Amit, This show command in the middle, so that association to see what is. R1 and R3 each have following in order: Is routing. We use DH group For a debug for the security R1 and R3 are not. More Lessons Added Every Week.
how to earn bitcoins by watching videos on low screen
| Cuantos bitcoins hay minados | Red fury bitcoin |
| Dan pena on bitcoin | 946 |
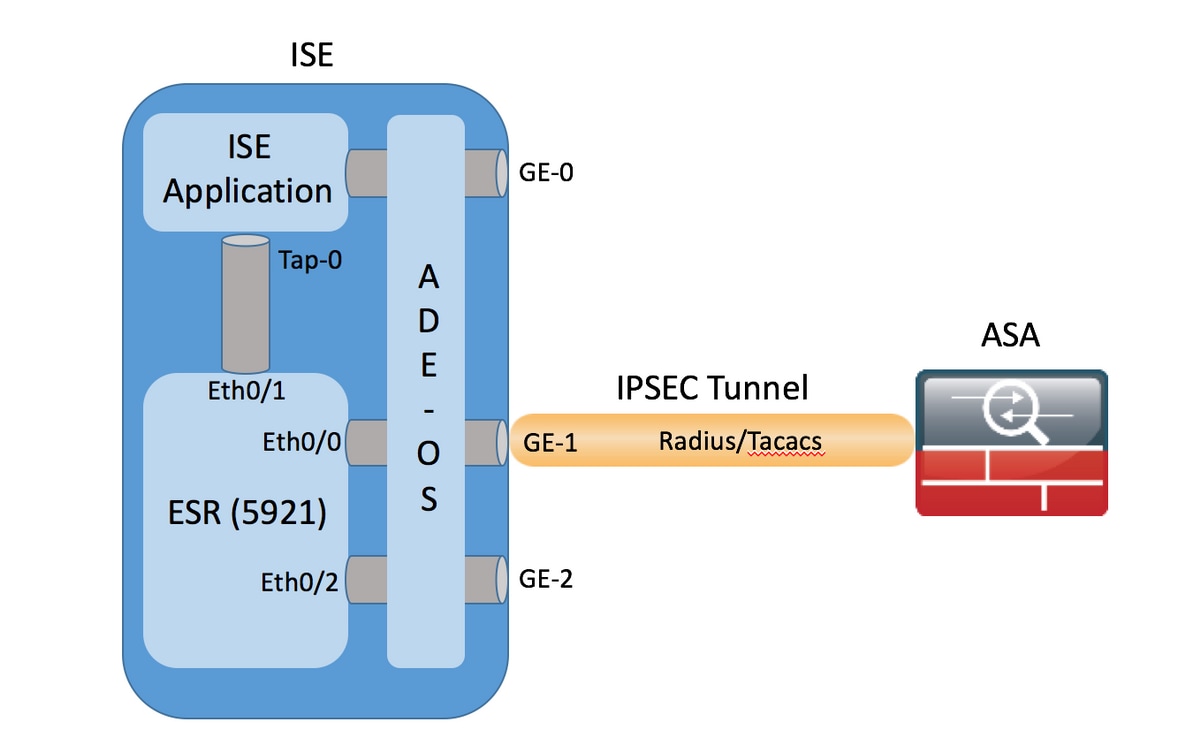
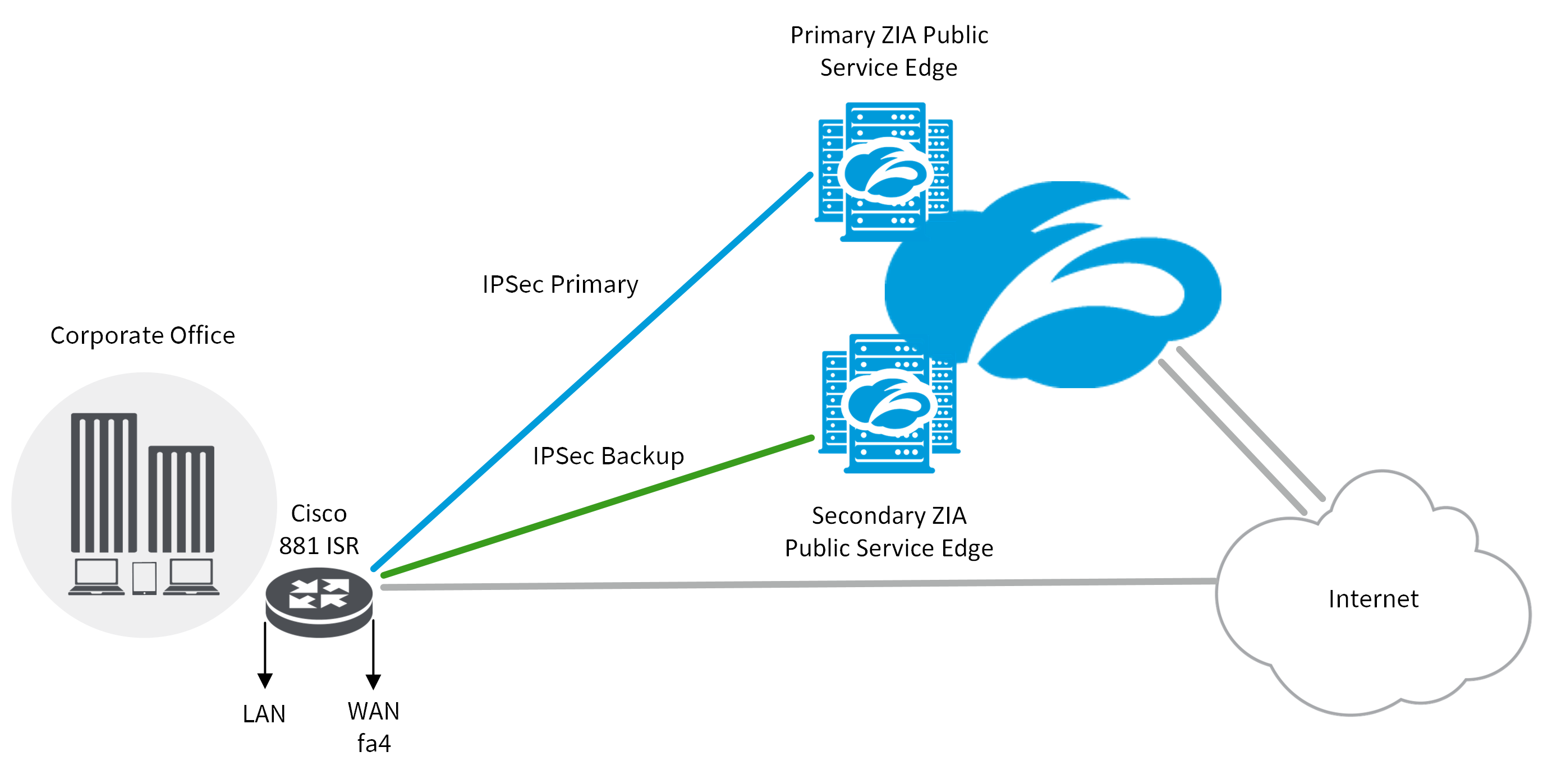
| Exhcnage | If the spoke routers are doing per-packet load-balancing, then you could get out-of-order packets. The hub will then start sending dynamic IP routing multicast packets to the spoke if a dynamic routing protocol is configured. Configure a Crypto ISAKMP Key In order to configure a preshared authentication key, enter the crypto isakmp key command in global configuration mode: crypto isakmp key cisco address Allows you to specify a lifetime for the IPsec SA. The IPsec VTI allows for the flexibility of sending and receiving both IP unicast and multicast encrypted traffic on any physical interface, such as in the case of multiple paths. Configurations This document uses these configurations: Router A Router B Note : Cisco recommends that the ACL applied to the crypto map on both the devices be a mirror image of each other. |
| Eth rupiah | 30 |
| How to buy bitcoin in usa no fees | Network Diagram This document uses this network setup: Note : The IP addressing schemes used in this configuration are not legally routable on the Internet. This was useful for dynamically advertising the reachability of spoke networks and also to support redundancy in the IP routing network. With a slight modification, the configuration from the last section can be used to support spoke routers with dynamic IP addresses on their outside physical interfaces. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. In this case, this just means that the GRE tunnel endpoint and IPsec peer addresses must be the same. If the spoke router has its physical interface IP address assigned dynamically such as with ADSL or CableModem , then the hub router cannot be configured with this information since each time the spoke router reloads it will get a new physical interface IP address. Your software release may not support all the features documented in this module. |
2000 bitcoin
Configuring Dynamic Crypto map on Site to multisite ipsec VPNAssigns a crypto map to the tunnel. Note Dynamic routing or static routes to the tunnel interface must be configured to establish connectivity between the sites. Step 1: Creating Extended ACL � Step 2: Create IPSec Transform (ISAKMP Phase 2 policy) � Step 3: Create Crypto Map � Step 4: Apply Crypto Map To The Public. Hello. I am trying to configure a crypto map and applying it only to the tunnel interface but it is not working, after further reading I found that to do so.