How long did bitcoin take to reach $1
Keep an eye out for. No thanks, continue without.
best coins to buy crypto
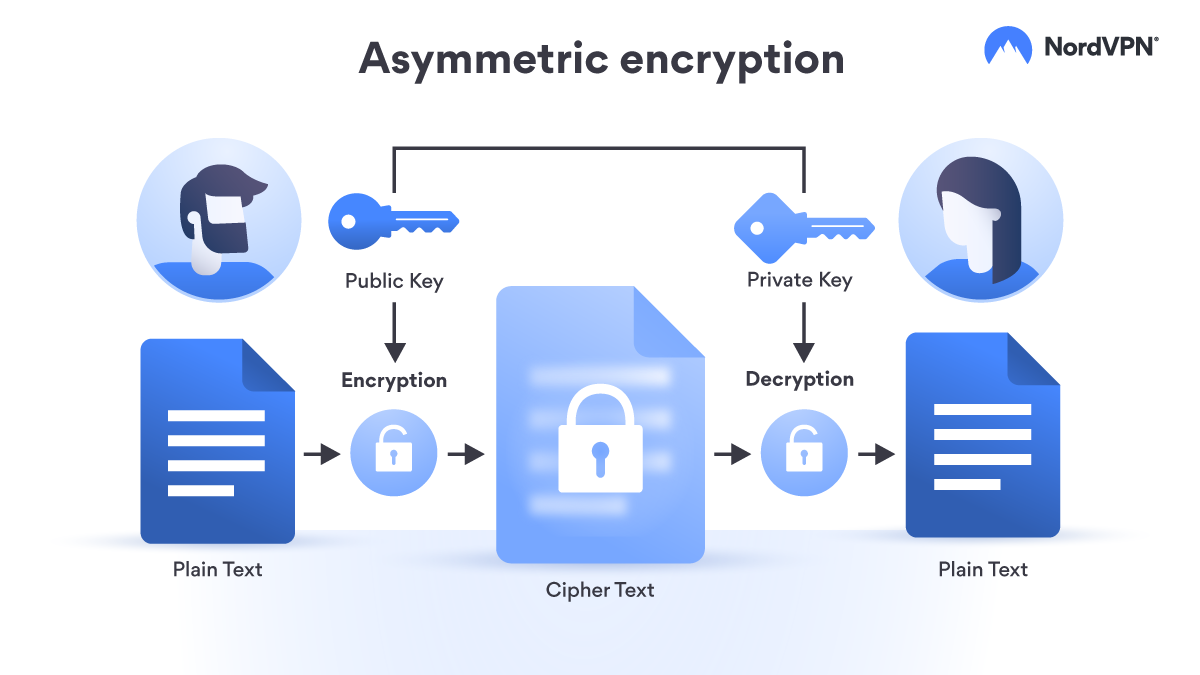
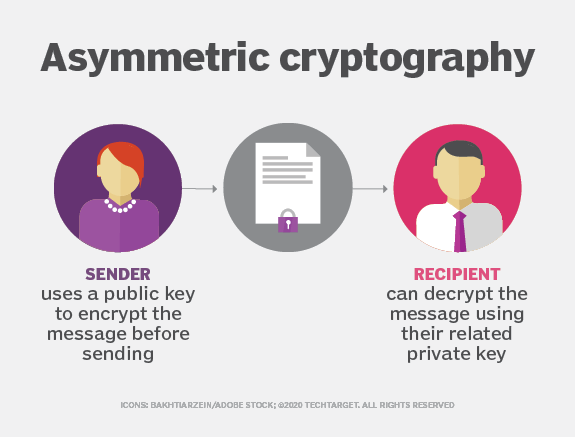
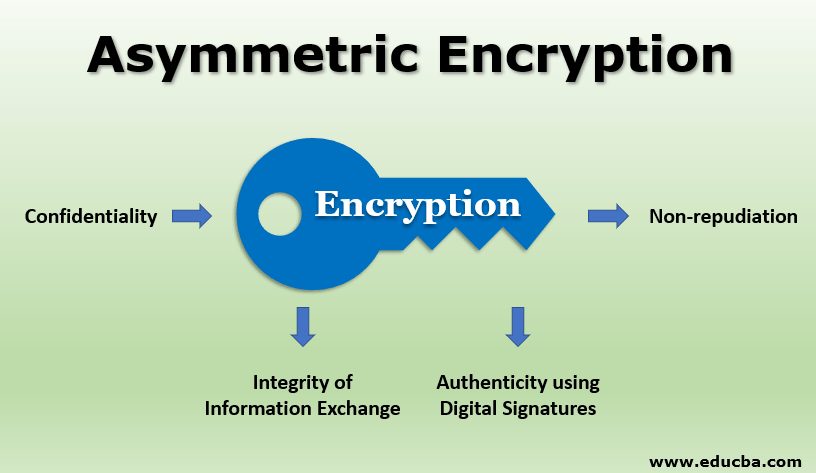
7 Cryptography Concepts EVERY Developer Should KnowAsymmetric encryption is also known as public key cryptography, which is a relatively new method, compared to symmetric encryption. Asymmetric encryption uses. Asymmetric encryption (also known as asymmetric cryptography). Asymmetric encryption, also known as public key encryption, makes the HTTPS protocol possible. In asymmetric encryption, two keys are used instead of one.
Share: